Potential losses from cyberattacks incurred by financial institutions have been estimated to range between 10% and 50% of their profits in a tail scenario (Lagarde, 2018). The magnitude of these numbers should be an alert for authorities in charge of financial stability. Yet cyber risk refers to a spectrum of threats extending well beyond the financial sector. In fact, successful cyberattacks against vital infrastructures such as hospitals, airports, and telecommunications could cause widespread disruptions involving large human and financial costs. Fortunately, the destructive impact of malicious attacks has so far been limited, but this should not lead to complacency.
When considering the challenge of cyber security, three distinct perspectives can be adopted:
- The strategic perspective sees cyberattacks in the context of interstate competition, or conflict, where cyberwarfare is increasingly used alongside conventional warfare, or even as a substitute for it.
- The operational perspective focuses on how to ensure the safety and continuity of specific information and communication technology (ICT) systems through the detection of threats, protection against attacks, as well as recovery and response after an incident. This is the main area of focus for financial regulators and supervisors.
- Finally, the global public good perspective looks into possible approaches to strengthen the international governance of cyber security.
Game theory offers valuable insights for each of these three viewpoints.
At the strategic level, defence policy experts have pointed out that states, as much as private companies, assert their jurisdiction over the cyberspace (Flournoy and Sulmeyer, 2018). State-sponsored cyberattacks have de facto been utilised as a vehicle for asymmetric belligerence. Classical deterrence theory emphasises the cost of conflict and the balance of power as key ingredients of stability. By contrast other recent approaches (“perfect deterrence” theory: Figure 1) stress the importance of the value of the status quo, and show that asymmetric power relationships can be very stable (Zagare, 2019). The main takeaway from this analysis is that negotiation with a potential cyber adversary should be “conditionally cooperative”, i.e. threaten to respond in kind if the other state does not cooperate.
Deterrence efforts may deflect attacks toward weaker targets
Yet non-state actors also perpetrate cyber crime. In this respect, game-theoretic tools used to analyse counterterrorist policies (surveyed in Sandler and Arce, 2007) are of interest. The literature highlights the externalities involved in such policies. Deterrence actions taken to protect alternative potential targets (be it governments or businesses) can have negative externalities if such defensive efforts result in attacks being deflected toward weaker targets. In contrast, pre-emptive policy actions (e.g. seeking to neutralise criminal capabilities, or freezing their assets) have positive externalities benefiting all targets, but may result in free riding. Such public good provision faces the risk of insufficient collective action.
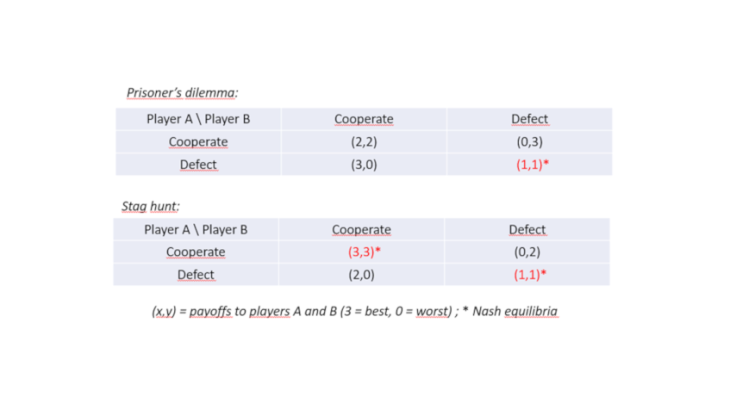
Figure 2 illustrates a simple cyber security coordination game: cooperative action means contributing to identifying and fixing security vulnerabilities. Non-cooperative behaviour corresponds to insufficient preventive action and possibly free riding on other actors’ efforts to deploy adequate protection. However, the choice of actions also depends on the extent of information sharing that is expected from other players, and the associated costs and benefits. Two versions of this game can be considered:
- The prisoner’s dilemma version, in which benefits from keeping private the information on threats drive non-cooperative behaviour, but result in a worse collective outcome.
- The ”stag hunt” version, in which the shared benefits from cyber resilience outweigh the benefits from keeping information private, but cooperative equilibrium still requires mutual trust.